XVisible

Complete set of highly encrypted communication tools that gives you full control of the information you exchange, based on the secure communication environment concept (SCE)

ALL-IN-ONE SECURE COMMUNICATION ENVIRONMENT
THAT GIVES PRIVACY TO BUSINESS
Secure peer to peer video/audio calls that can run from any device or platform without using any applications.
Your browsing activities will be inaccessible to anyone who is spying on your network, including your internet service provider.
Untraceable calls at a minimum cost to any phone in the world using any browser in any device

Complete set of highly encrypted communication tools that gives you full control of the information you exchange, based on the secure communication environment concept (SCE)
Encryption "on-the-fly" makes tranferring files secure and your files inaccessible to intruders
Makes it possible to securely exchange chat messages because all messages are heavily encrypted by default.
A secure e-mail service for xvisible users with the highest-grade of encryption
|
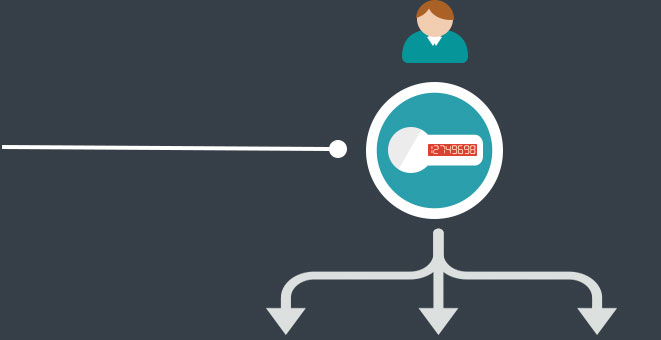
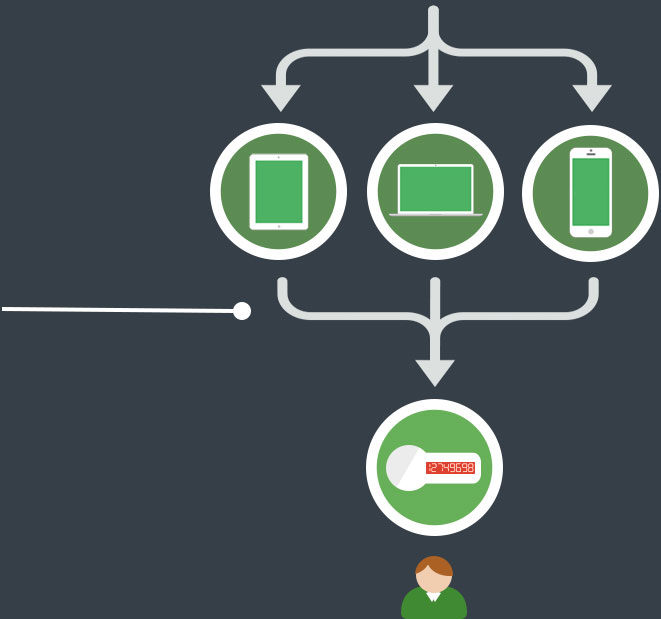
Every user has an OTP token that provides a password to XVisible. The password changes every 27 seconds. |
 |
|
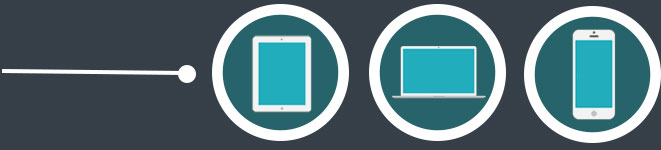
Using the password from your OTP token, you can access the system with any browser in any device without installing any applications. |
 |
|
Transport Layer Security connection (TLS) with elliptic curve Diffie–Hellman (ECDH) cryptography protocol with perfect forward secrecy (PFS) makes sure that communication is secure. Messages are protected with Off-the-Record Messaging (OTR) |
 |
|
After you log in to XVisible’s Secure communication Environment, you gain access to a range of communication services sealed in one highly secure system. |
 |
|
All actions in the system are fully anonymous. The architecture of the system is such that even its creators and administrators do not have the technical possibility to track users’ actions or to store their personal data |
 |